OpenID is an open standard of a decentralized authentication system that allows the user to create a single account for authenticating to multiple unrelated Internet resources.
To set up OpenID authorization on the Picvario website:
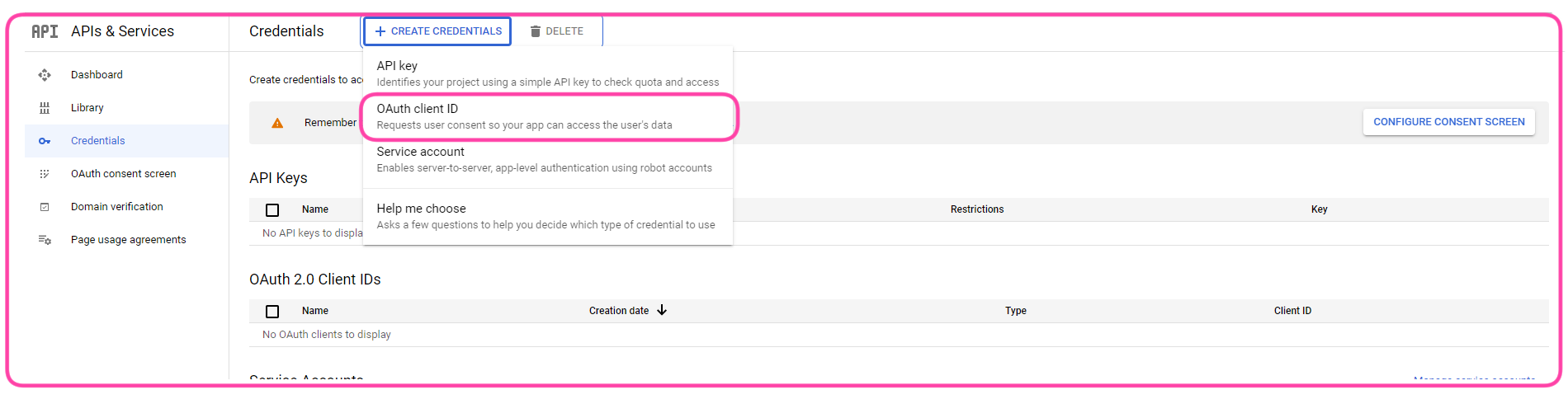
Configure settings on Google:
- Go to https://console.developers.google.com/apis/credentials using your organization’s administrator account.
- Create a new web application (for example, named Picvario).
- Get the ClientID and Client Secret in the control panel:
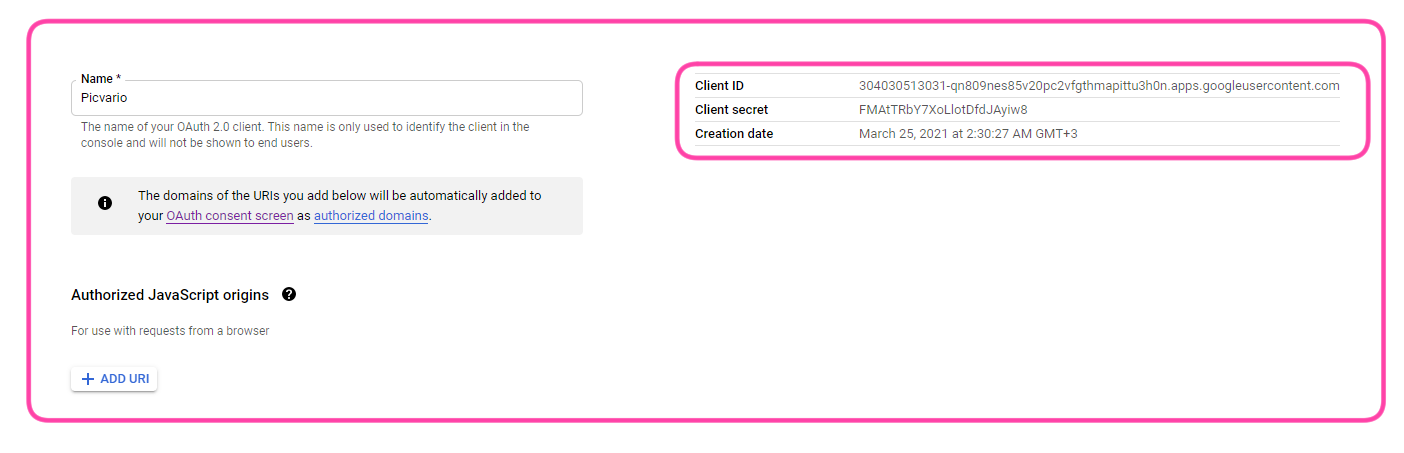
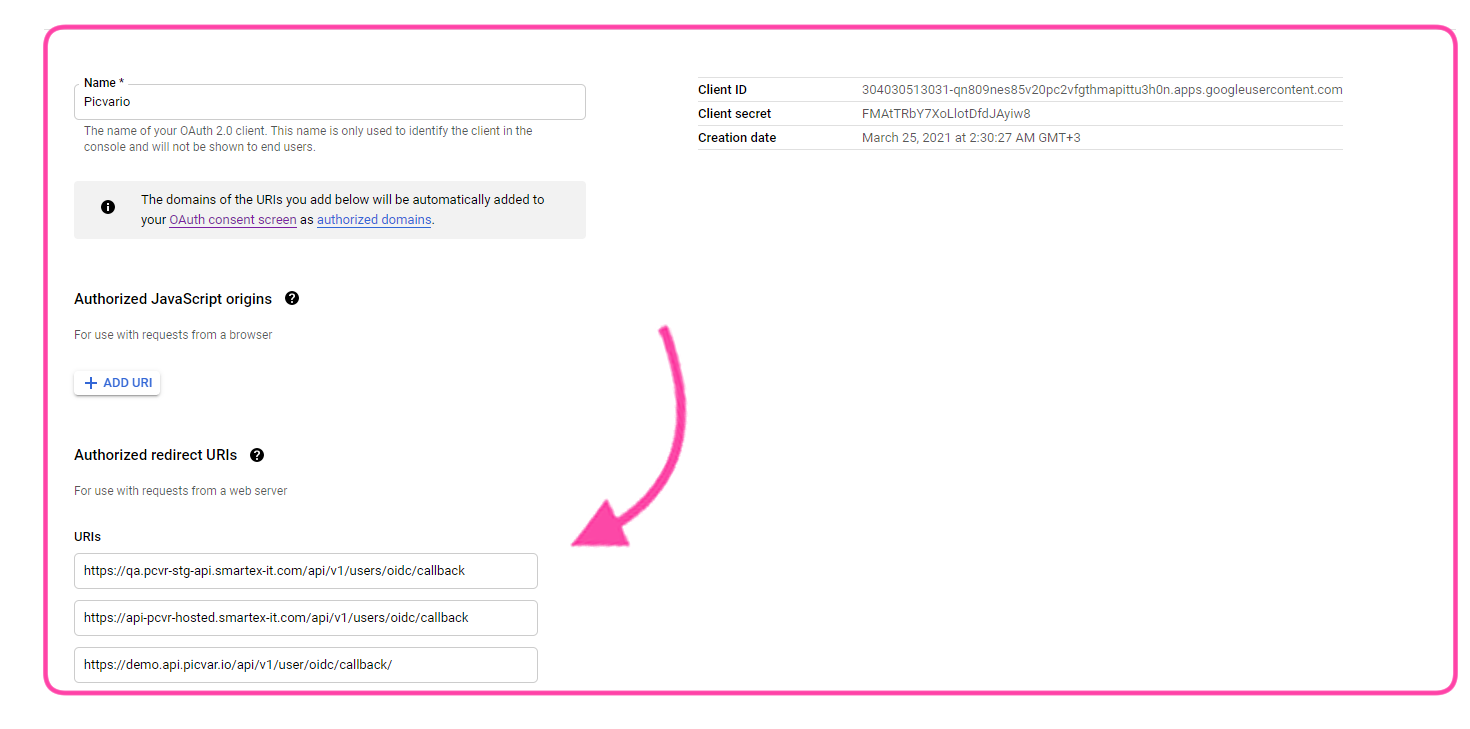
- Add the following address to the list of authorized URIs:
<site_url>/api/v1/users/oidc/callback
Configure settings on Picvario:
- Copy the environment variable from frontend SITE_BASE_URL=< some url >.
- In the tenant’s Options ( https://<tenant-name>.<site_url>/admin/options/option/) or in hosted versions ( https://<site_url>/admin/options/option/ ), create the parameter:
OPENID_AUTH_ENABLED
After the parameter is added, 11 more parameters will be created AUTOMATICALLY. You will need to change their values to:
| KEY | VAL | PUBLIC | |
| OIDC_TOKEN_USE_BASIC_AUTH | True | | |
| OIDC_RP_SIGN_ALGO | RS256 | | |
| OIDC_RP_SCOPES | email profile openid | | |
| OIDC_RP_CLIENT_SECRET | (from Google) | | |
| OIDC_RP_CLIENT_ID | (from Google) | | |
| OIDC_OP_USER_ENDPOINT | https://openidconnect.googleapis.com/v1/userinfo | | |
| OIDC_OP_TOKEN_ENDPOINT | https://oauth2.googleapis.com/token | | |
| OIDC_OP_JWKS_ENDPOINT | https://www.googleapis.com/oauth2/v3/certs | | |
| OIDC_OP_AUTHORIZATION_ENDPOINT | https://accounts.google.com/o/oauth2/v2/auth | |
IMPORTANT! The Public property of all of the above-mentioned options must have the False value! (set by default)
If you want to allow anonymous users to view assets, use ALLOW_ANONYMOUS_USERS = True. This parameter must be public (Public = True) regardless of the value of the parameter itself.
To allow authorization BOTH via Gsuite AND via Picvario, the MULTI_AUTH parameter is used. This parameter is also public (Public = True).
MULTI_AUTH=True/False
- parameter that determines whether authentication is possible using several available methods: standard and via OpenID. In the UI, this option is displayed as a page with the standard login and password fields and an additional button at the bottom: «Sign in via corporate account». When the value is False, the authentication option is determined by the OPENID_AUTH_ENABLED.
Sequence of public key search for token verification / Option Priority:
-
OIDC_RP_IDP_SIGN_KEY_PATH
-
OIDC_RP_IDP_SIGN_KEY
-
OIDC_OP_JWKS_ENDPOINT
If errors such as
SuspiciousOperation
or
JWS token verification
failed appear, make sure there is no conflict between these options.
Only
OIDC_OP_JWKS_ENDPOINT
should be specified for GSuite. Other options in this list should be left empty!